1 Deploying - deploy the latest version
2 BACKUP
3 CHECK MEMORY
4 Patching - How to fix CVE-2016-1287 - Cisco ASA Software IKEv1 and IKEv2 Buffer Overflow Vulnerability - https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160210-asa-ike
4.1 How to patch Cisco ASA5505 and ASA5510
4.2 How to patch Cisco ASA550x-X Models
5 Firewall Upgrade
6 Boot Order - Failback
7 Updating HA pairs
8 Compatibility Matrix
9 Upgrade path and steps
10 Bugtrack
How to patch and upgrade Cisco ASA to fix CVE-2016-1287?
This page is about how patch Cisco ASA to fix latest vulnerabilities.
This is also a guide how to deploy firewalls to be on the latest version from start.
This is also a guide to perform upgrade from 8.2 to 9.1 (going through 8.4 is absolutely critical)
Not every image is good for a firewall so here you find how to setup a failback image in case the new image won't boot.
Deploying - deploy the latest version
ASA5505: (stable)
copy http://nfsec.co.uk/cisco/asa5505/asa917-k8.bin disk0:/asa917-k8.bin
OR
copy http://nfsec.co.uk/cisco/asa5505/asa924-k8.bin disk0:/asa924-k8.bin
copy http://nfsec.co.uk/cisco/asdm-752-153.bin disk0:/asdm-752-153.bin
conf t
boot system disk0:/asa917-k8.bin
asdm image disk0:/asdm-752-153.bin
exit
reload save-config noconfirm
ASA5505: (latest interim - latest available security fixes)
copy http://nfsec.co.uk/cisco/asa5505/interim/asa924-8-k8.bin disk0:/asa924-8-k8.bin
(26-FEB-2016 http://www.cisco.com/web/software/280775065/129558/ASA-924-Interim-Release-Notes.html)
copy http://nfsec.co.uk/cisco/asa5505/interim/asa916-11-k8.bin disk0:/asa916-11-k8.bin
(16-FEB-2016 http://www.cisco.com/web/software/280775065/123352/ASA-916-Interim-Release-Notes.html)
ASA5510: (stable)
copy http://nfsec.co.uk/cisco/asa5510/asa917-k8.bin disk0:/asa917-k8.bin
copy http://nfsec.co.uk/cisco/asdm-752-153.bin disk0:/asdm-752-153.bin
conf t
boot system disk0:/asa917-k8.bin
asdm image disk0:/asdm-752-153.bin
exit
reload save-config noconfirm
ASA5510: (latest interim - latest available security fixes)
copy http://nfsec.co.uk/cisco/asa5510/interim/asa924-8-k8.bin disk0:/asa924-8-k8.bin
copy http://nfsec.co.uk/cisco/asa5510/interim/asa917-4-k8.bin disk0:/asa917-4-k8.bin
(26-FEB-2016 http://www.cisco.com/web/software/280775065/129558/ASA-924-Interim-Release-Notes.html)
copy http://nfsec.co.uk/cisco/asa5510/interim/asa916-11-k8.bin disk0:/asa916-11-k8.bin
(16-FEB-2016 http://www.cisco.com/web/software/280775065/123352/ASA-916-Interim-Release-Notes.html)
ALL 550X-X MODELs (STABLE)
copy http://nfsec.co.uk/cisco/asa5515x/asa952-smp-k8.bin disk0:/asa952-smp-k8.bin
copy http://nfsec.co.uk/cisco/asdm-752-153.bin disk0:/asdm-752-153.bin
conf t
boot system disk0:/asa952-smp-k8
asdm image disk0:/asdm-752-153.bin
exit
reload save-config noconfirm
ALL 550X-X MODELs (latest interim - latest available security fixes)
copy http://nfsec.co.uk/cisco/asa5515x/asa952-5-smp-k8.bin disk0:/asa952-5-smp-k8.bin
copy http://nfsec.co.uk/cisco/asa5515x/asa942-11-smp-k8.bin disk0:/asa942-11-smp-k8.bin
BACKUP
Take a full firewall backup before you patch or upgrade either using ASDM or command line:
ASDM: >>Tools > Backup Configuration >> Backup All
CLI: more system: running-config
CHECK MEMORY
Check Memory of device - http://www.cisco.com/c/en/us/products/collateral/security/asa-5500-series-next-generation-firewalls/productbulletinc25-586414.html
Also a useful link: https://supportforums.cisco.com/document/48646/asa-83-upgrade-what-you-need-know
How to patch Cisco ASA5505 and ASA5510
Patch ASA 8.2(1-5)
To an old device running ASA 8.2(5) image you should only apply the interim new image as follows:
copy http://nfsec.co.uk/cisco/asa825-59-k8.bindisk0:/asa825-59-k8.bin
Patch ASA 8.4(1-6)
To an old device running ASA 8.4(5) image you should only apply the interim new image as follows:
copy http://nfsec.co.uk/cisco/asa847-30-k8.bindisk0:/asa847-30-k8.bin
Patch ASA 8.4(5) and later via direct upgrade to 9.1(7) STABLE or 9.2(4)8 INTERIM
copy http://nfsec.co.uk/cisco/asa917-k8.bin disk0:/asa917-k8.bin
OR
copy http://nfsec.co.uk/cisco/asa924-8-k8.bin disk0:/asa924-8-k8.bin
Note: The ASDM should be at least asdm-722.bin.
The above instructions are only how to patch the specific version 8.2(1-5) and 8.4(1-6).
How to patch Cisco ASA550x-X Models
copy http://nfsec.co.uk/cisco/asa5515x/asa952-5-smp-k8.bin disk0:/asa952-5-smp-k8.bin
copy http://nfsec.co.uk/cisco/asa5515x/asa942-11-smp-k8.bin disk0:/asa942-11-smp-k8.bin
Do not CONFUSE securing patching with upgrading (however some times upgrade may fix security flows (sic!)).
Firewall Upgrade
Many old ASA Images running on ASA5505 and ASA5510 requires upgrade.
Older version 8.2 - 8.4 - 8.5 - 8.6 have reached End of Software Maintenance. Customers should migrate to a supported release.
Cisco came up with an upgrade path to address NAT translation changes between old 8.2(x) version and newer 8.4(6) and forward.
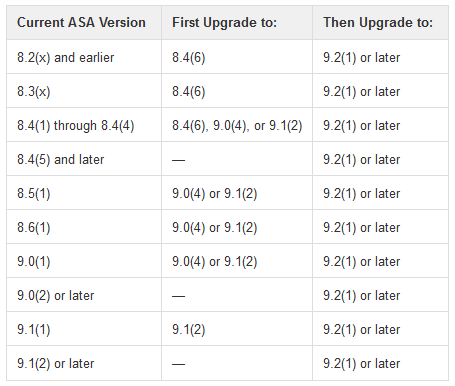
If the firewall is anywhere below: 8.4(6) or is 8.5(1) or 8.6(1) it has to go via upgrade path to the minimum version 9.2(1) as shown below.
If you are going via upgrade path I suggest to use ASDM 7.2(2) as a minimum before you upgrade ASDM to a higher version.
copy http://nfsec.co.uk/cisco/asdm-722.bin disk0:/asdm-722.bin
Upgrade the old 8.2(x) - 8.4.(4), or 8.5.1 or 8.6.1 or 9.0(1) or 9.1(1) to 9.2(1)
This is absolutely critical that you follow the upgrade path. The First Upgrade image will do the old style NAT conversion to the one which is then supported in 9.2(1).
Not doing this may have severe impact on the traffic flow.
Boot Order - Failback
Whenever you are patching or upgrading...
It is absolutely critical to setup a fail-back image in case your new image will not boot.
NFSEC-ASA1# show run | inc boot
boot system disk0:/asa917-k8.bin
boot system disk0:/asa914-k8.bin
In the example above asa914-k8.bin was upgraded to asa917-k8.bin. The asa914-k8.bin was kept as a fail-back.
To setup/reverse it for example do:
no boot system disk0:/asa917-k8.bin
boot system disk0:/asa917-k8.bin
This will change the order to:
NFSEC-ASA1# show run | inc boot
boot system disk0:/asa914-k8.bin
boot system disk0:/asa917-k8.bin <-- has been drop to the second line.
Always keep currently working image as a fail-back.
Updating HA pairs
Primary: The primary firewall always refers to ASA1 regardless if it is in an active or standby state.
Secondary: The secondary firewall always refers to ASA2 regardless if it is in an active or standby state.
Active: The firewall currently carrying the live traffic.
Standby: The passive firewall is the standby device awaiting to take over in the place of failure.
1.Upload the new firmware to both ASA's before proceeding.
2.Log into the Active firewall
3.Run the command (you will need to enable if you are on via ssh)
active# conf t
active# no boot system disk0:/asa846-k8.bin (the old boot)
active# boot system disk0:/asa847-30-k8.bin (the new interim image or stable with security fix)
active# boot system disk0:/asa846-k8.bin (KEEP FAILBACK - the old boot)
active# exit
4.Then save it with the two commands
active# write mem
active# write standby
5.Then reboot the secondary firewall (make sure the image is on the disk0:)
active# failover exec standby reload noconfirm
6.Use the command
active# sh fail
7.Wait for the secondary firewall to finish rebooting
Once show fail is showing the other firewall as
Other host: Secondary - Standby Ready
1.Then we can failover to reboot the primary
2.This is done with
primary# no failover active
3.Once you run that command you will be disconnected from the firewall simply reconnect. Once you get on confirm that the firewall has failed over with
active# sh fail
4.It should say
This host: Secondary - Active
5.If it does send the other firewall for a reboot with
active# failover exec standby reload noconfirm
Then wait for sh fail to show the other firewall in the ready state and once it is fail back over to the primary
active# no failover active
Compatibility Matrix
http://www.cisco.com/c/en/us/td/docs/security/asa/compatibility/asamatrx.html
Upgrade path and steps
http://www.cisco.com/c/en/us/td/docs/security/asa/asa92/upgrade/upgrade92.html
Bugtrack
CVE-2016-1287: https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20160210-asa-ike
Published: 2016 February 10 16:00 GMT