You have already deployed OpenLDAP following the other post did you?
Great, because now you will have to manage it.
You cannot admit that management of .ldif and creating the Directory objects and attributes is an easy task.
Perhaps it is however there is a simpler way to manage it.
In this post I will walk through deploying PHPLDAPADMIN - a tool which helps administering the OpenLDAP via Web GUI.
Furthermore, will use it to create OU and CN in it.
Finally, I will complete the concept of using OpenLDAP with LDAPS protocol and Linux sudoers PAM intergration.
1. PHPLDAPADMIN
Installation of phpldapadmin is as simple as:
yum install phpldapadmin
After installation you will need to allow access to GUI by modifying the below file and completing some basic pre-requisite steps.
vi /etc/httpd/conf.d/phpldapadmin.conf
<IfModule !mod_authz_core.c>
# Apache 2.2
Order Allow,Deny
Allow from 127.0.0.1
Allow from ::1
Allow from x.x.x.0/24
Deny from all
</IfModule>
cd /usr/share/phpldapadmin/
chown -R apache:apache phpldapadmin/
chown apache:apache phpldapadmin/
setsebool httpd_can_connect_ldap on
Later you need to configure phpldapadmin configuration file to point to your ldap server over LDAPS protocol.
vi /etc/phpldapadmin/config.php
$servers->newServer('ldap_pla');
$servers->setValue('server','name','Local LDAP Server');
$servers->setValue('server','host','ldaps://Your_FQDN:636');
$servers->setValue('server','port',0);
$servers->setValue('server','base',array('dc=hextrim,dc=com'));
$servers->setValue('login','auth_type','session');
$servers->setValue('login','bind_id','cn=admins,dc=hextrim,dc=com');
$servers->setValue('server','tls',false);
$servers->setValue('login','attr','dn');
$servers->setValue('appearance','password_hash','');
Note that the config file is long and you need to "unhash" only the above to make it working
You can then simply start apache and login to the GUI with your cn=admins (Manager) password.
2. OpenLDAP Server with Sudoers Schema.
The reason behind deploying this is to have the ability to use only one user on all of your infrastructure servers and give this user sudo rights without updating the /etc/sudoers file each time on every server manually. Now, these days you could use tools like ansible to do it however it is not said that OpenLDAP usage must be only for posixGroup user access and OpenLDAP is therefore only good at it. OpenLDAP integration should be extended to every centralized system you got deployed and your only one "admin" user access to everything in your infrastructure wide systems.
There are only few steps required to prepare your OpenLDAP server for that sudoers integration.
rpm -ql sudo
cat /usr/share/doc/sudo-1.8.6p7/schema.OpenLDAP
cp /usr/share/doc/sudo-1.8.6p7/schema.OpenLDAP /etc/openldap/schema/sudo.schema
vi /etc/openldap/slapd.conf
slaptest -f /etc/openldap/slapd.conf -F /tmp/
cd /tmp/cn\=config/cn\=schema/
cp cn\=\{0\}sudo.ldif /etc/openldap/slapd.d/sudo.ldif
cd /etc/openldap/slapd.d/
vi sudo.ldiff
Change:
dn: cn={0}sudo
objectClass: olcSchemaConfig
cn: {0}sudo
To:
dn: cn=sudo,cn=schema,cn=config
objectClass: olcSchemaConfig
cn: sudo
From the end of file remove:
structuralObjectClass: olcSchemaConfig
entryUUID: 58087688-8b2f-1036-92f4-6bd39bbe0a22
creatorsName: cn=config
createTimestamp: 20170219204007Z
entryCSN: 20170219204007.401828Z#000000#000#000000
modifiersName: cn=config
modifyTimestamp: 20170219204007Z
Next, enable LDAPI again and import your sudo.ldif (schema) to your Directory
ldapadd -Y EXTERNAL -W -H ldapi:/// -f sudo.ldif
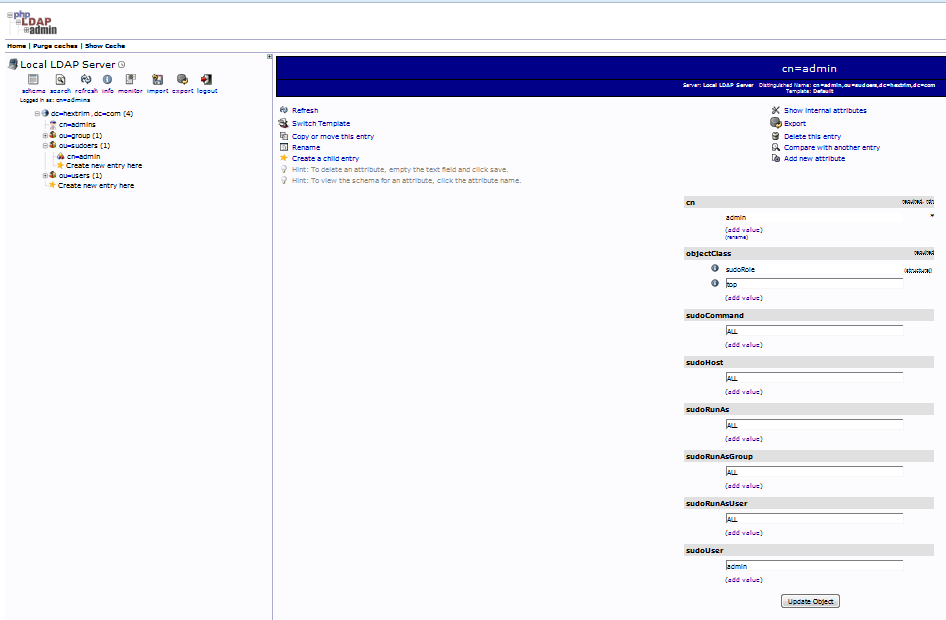
Finally, login to PHPLDAPADMIN and create ou=sudoers and cn= record for your "admin" user.
3. OpenLDAP Client with Sudoers and PAM integration.
On the client side there are two additional steps you are required to do. (Additional to what you already configured following my other post)
You need to add:
[root@localhost ~]# cat /etc/nsswitch.conf
sudoers: ldap files
You need to provide:
[root@localhost ~]# cat /etc/sudo-ldap.conf
uri ldaps://FQDN_LDAP_SERVER
tls_cacertfile /etc/openldap/cacerts/cacert.pem
sudoers_base ou=sudoers,dc=hextrim,dc=com
debug 2
Now after successful login with "admin" user try sudo access.
[admin@localhost ~]$ sudo -i
LDAP Config Summary
===================
uri ldaps://FQDN_LDAP_SERVER
ldap_version 3
sudoers_base ou=sudoers,dc=hextrim,dc=com
binddn (anonymous)
bindpw (anonymous)
ssl (no)
tls_cacertfile /etc/openldap/cacerts/cacert.pem
===================
sudo: ldap_set_option: debug -> 0
sudo: ldap_set_option: tls_cacertfile -> /etc/openldap/cacerts/cacert.pem
sudo: ldap_set_option: tls_cacert -> /etc/openldap/cacerts/cacert.pem
sudo: ldap_initialize(ld, ldaps://FQDN_LDAP_SERVER)
sudo: ldap_set_option: ldap_version -> 3
sudo: ldap_sasl_bind_s() ok
sudo: Looking for cn=defaults: cn=defaults
sudo: no default options found in ou=sudoers,dc=hextrim,dc=com
sudo: ldap search '(|(sudoUser=admin)(sudoUser=#1000)(sudoUser=%admins)(sudoUser=%#1000)(sudoUser=ALL))'
sudo: searching from base 'ou=sudoers,dc=hextrim,dc=com'
sudo: adding search result
sudo: ldap sudoHost 'ALL' ... MATCH!
sudo: result now has 1 entries
sudo: ldap search '(sudoUser=+*)'
sudo: searching from base 'ou=sudoers,dc=hextrim,dc=com'
sudo: adding search result
sudo: result now has 1 entries
sudo: sorting remaining 1 entries
sudo: searching LDAP for sudoers entries
sudo: ldap sudoRunAsUser 'ALL' ... MATCH!
sudo: ldap sudoCommand 'ALL' ... MATCH!
sudo: Command allowed
sudo: LDAP entry: 0x7f06e45a3b10
sudo: done with LDAP searches
sudo: user_matches=1
sudo: host_matches=1
sudo: sudo_ldap_lookup(0)=0x02
[sudo] password for admin: *********
sudo: removing reusable search result
[root@localhost ~]#
In the logs you will see that previous attempts showed that your user was not in sudoers file and now it is.
Before:
cat /var/log/secure
Feb 20 08:59:57 localhost unix_chkpwd[8633]: password check failed for user (admin)
Feb 20 08:59:57 localhost sudo: pam_unix(sudo:auth): authentication failure; logname=admin uid=1000 euid=0 tty=/dev/pts/0
ruser=admin rhost= user=admin
Feb 20 08:59:57 localhost sudo: pam_ldap(sudo:auth): Authentication failure; user=admin
Feb 20 09:00:01 localhost sudo: pam_unix(sudo:auth): conversation failed
Feb 20 09:00:01 localhost sudo: pam_unix(sudo:auth): auth could not identify password for [admin]
Feb 20 09:00:01 localhost sudo: pam_ldap(sudo:auth): failed to get password: Authentication failure
Feb 20 09:00:01 localhost sudo: admin : user NOT in sudoers ; TTY=pts/0 ; PWD=/home/admin ; USER=root ; COMMAND=/bin/su -
After:
cat /var/log/secure
Feb 20 09:51:57 localhost sudo: pam_unix(sudo:auth): authentication failure; logname=admin uid=1000 euid=0 tty=/dev/pts/0
ruser=admin rhost= user=admin
Feb 20 09:52:11 localhost sudo: admin : TTY=pts/0 ; PWD=/home/admin ; USER=root ; COMMAND=/bin/su -
Feb 20 09:52:11 localhost su: pam_unix(su-l:session): session opened for user root by admin(uid=0)
Feb 20 09:52:15 localhost su: pam_unix(su-l:session): session closed for user root
By these few steps you achieved OpenLDAP / PHPLDAPADMIN deployment and sudoers schema integration for ease of further infrastructure management.
--- lo3k